Crackme 3: Windows binary (PE)
⚠️ This crackme is from a website that has a leaderboard. Please do not cheat.
Link: https://www.root-me.org/en/Challenges/Cracking/PE-0-protection (binary)
Our first PE (Windows) binary. We won’t be able to run it in Docker, so let’s try to use Hopper exclusively.
Starting with the strings tab, there are interesting values we can follow:
A chain of single-byte comparisons all either continue ahead or short-circuit the program to print “wrong password”:
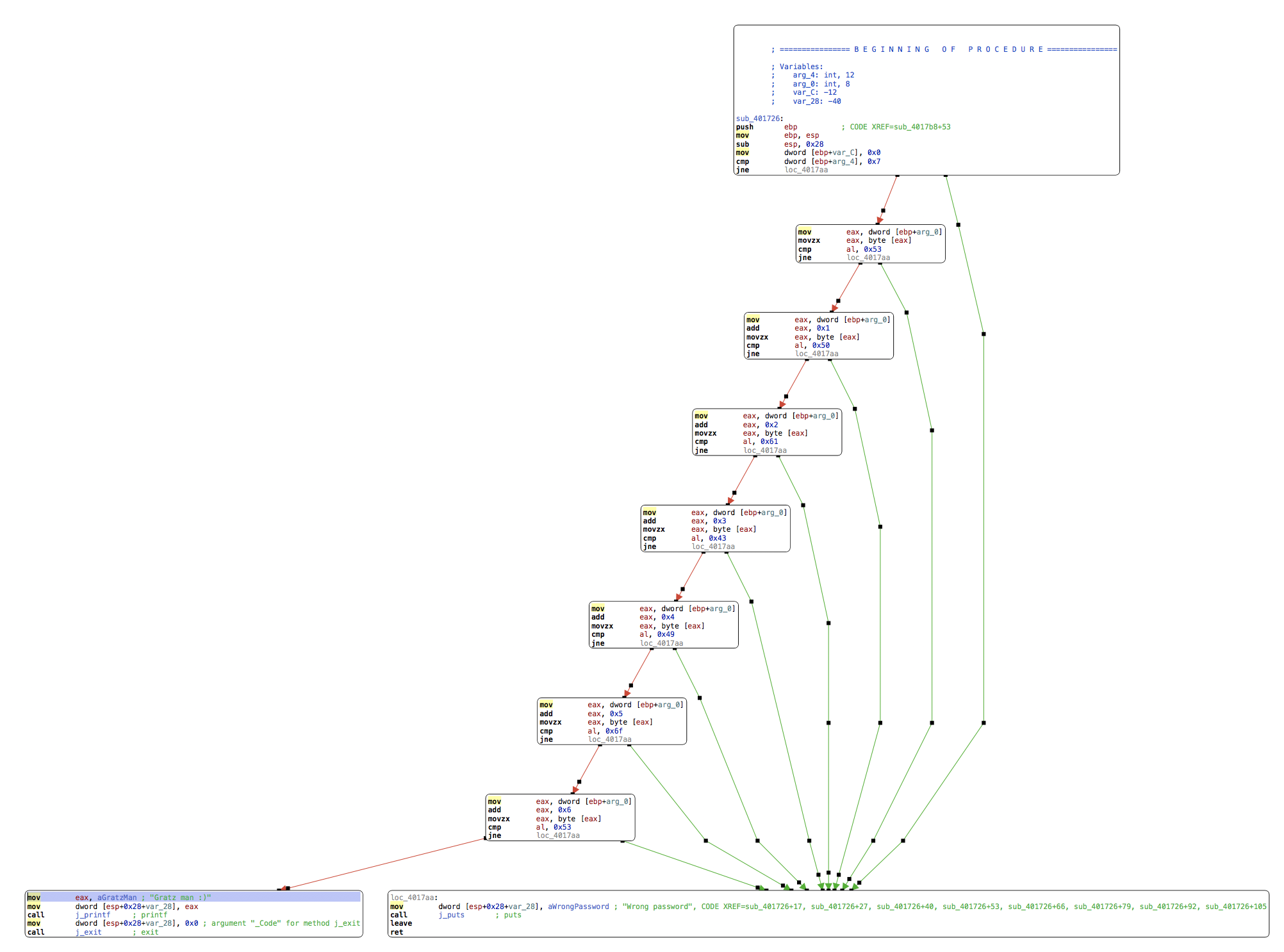
They compare a buffer byte by byte to a expected value, looking for the following sequence: 0x53, 0x50, 0x61, 0x43, 0x49, 0x6f, 0x53.
>>> ''.join(map(chr, [0x53, 0x50, 0x61, 0x43, 0x49, 0x6f, 0x53]))
'SPaCIoS'
A bit too easy.